Application whitelisting is a simple process of listing the applications that are granted permissions from the administrator or the user. When an application is executed, it is automatically checked against the whitelist, it is allowed to run. Whilst application whitelisting is incorrectly considered as a last moment security tool by many, it offers a high degree of flexibility. Many businesses fail to understand that Whitelisting holds equal importance as that of the other security parameters.
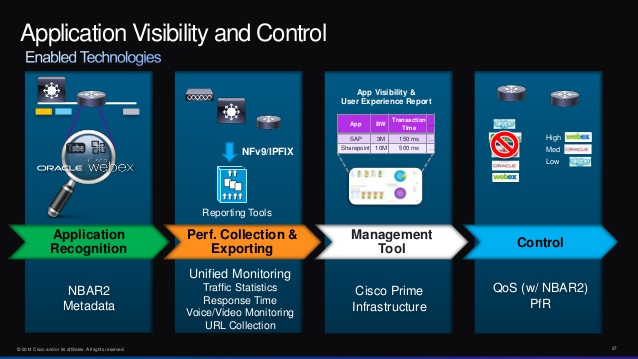
Importance of Application Whitelisting
Application whitelist can be generated in an automatic manner, either by using reference lists or manually by adding required programs to the administrative panel. Instead of blacklisting the applications, Whitelisting the programs can also help in monitoring the applications and software systems, whose locations or attributes mismatch with the Whitelisting perimeters. It enables the organizations to collect data about the working and location of the programs that are running over a network. In addition to uncovering potential vulnerabilities to the network and enabling application visibility and control; application whitelisting also enables to reveal the applications run sneakily by the employees. Since most of the large scale organizations, use same suite of applications on a daily basis, anomalies that are unveiled by the monitoring of applications can be quite revealing. Vigilant monitoring of all the applications is one of the best defense techniques against potential threats.
A Valuable Tool
Therefore, application whitelisting is considered to be one of the most important assets for ensuring system intelligence and endpoint security. The organizations which deploy application whitelisting just for the task of system intelligence can apply more strict policies on the applications after reviewing the report.
Since majority of cyber crimes are done by the malicious third parties, organizations need to contend with the inside threats. A former employer having a grudge against the company may find it very easy to make his way through the network and cause potential damage to the organization data. Moreover a current employer may have intimate knowledge about the IT system of the organization and it will be very easy for them to have access to the network.
Whilst firewalls, anti-viruses, Therefore, instead of investing in recovering data after a security breach, it is more feasible to invest in application visibility and control by means of application whitelisting.
Conclusion
There exists no unanimity among the security experts about the best technique which has to be used for saving the organization from falling prey to the security threats. The supporters of blacklisting assume that whitelisting is too difficult to manage and complex as well. On the other hand, the proponents of whitelisting believe that it is better to invest in protecting the systems from potential threat rather than investing in coping up with its aftermath. This is where blacklisting fails. Since the cyber attacks on the cloud-based databases hold the potential to impact the users working across multiple platforms and networks, the security pros who have been depending on other resources are surely to adopt application whitelisting for application visibility and control.

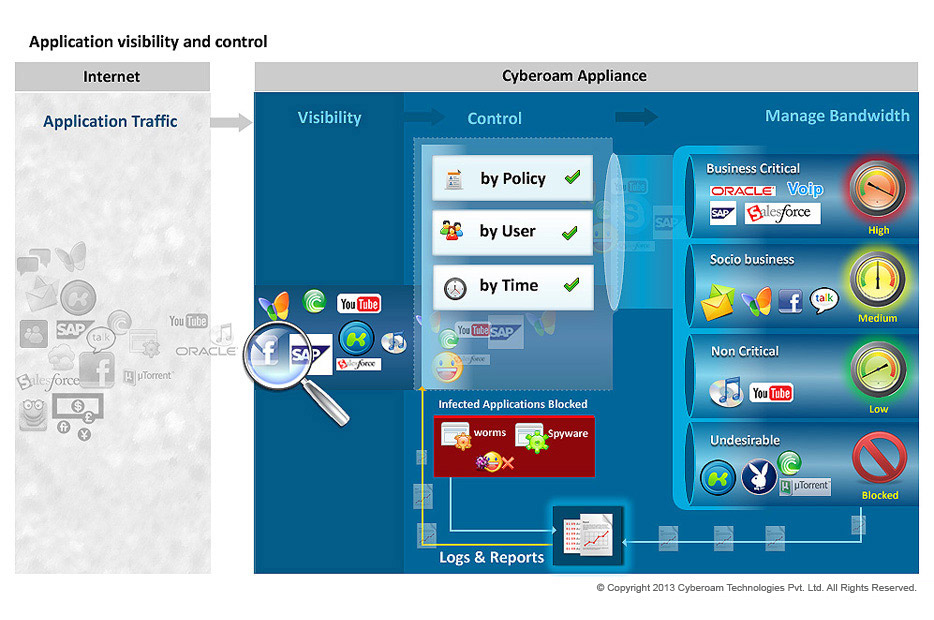




Leave a Reply